Closed
Description
Hi guys,
I am a new user of Casbin, I have some confusions about the role inheritance with RBAC model. For example:
If I have two roles just like that:
role:admin --> has permission: resource1, read
role:area_admin --> which inherited by role:admin and has permission: resource2, write
I expected that using role name(role:admin) can list all of sub permissions, the result has 2 rows:
- permission: resource1, read
- permission: resource2, write
BUT now, what I listed just ONLY one row in result: permission: resource1, read by golang API.
why?
Activity
hsluoyz commentedon Sep 28, 2018
I have added a new function in RBAC API called
GetImplicitPermissionsForUser(). It can retrieve all implicit permissions, see example here: 6dde83bg0194776 commentedon Sep 30, 2018
@hsluoyz thank you.
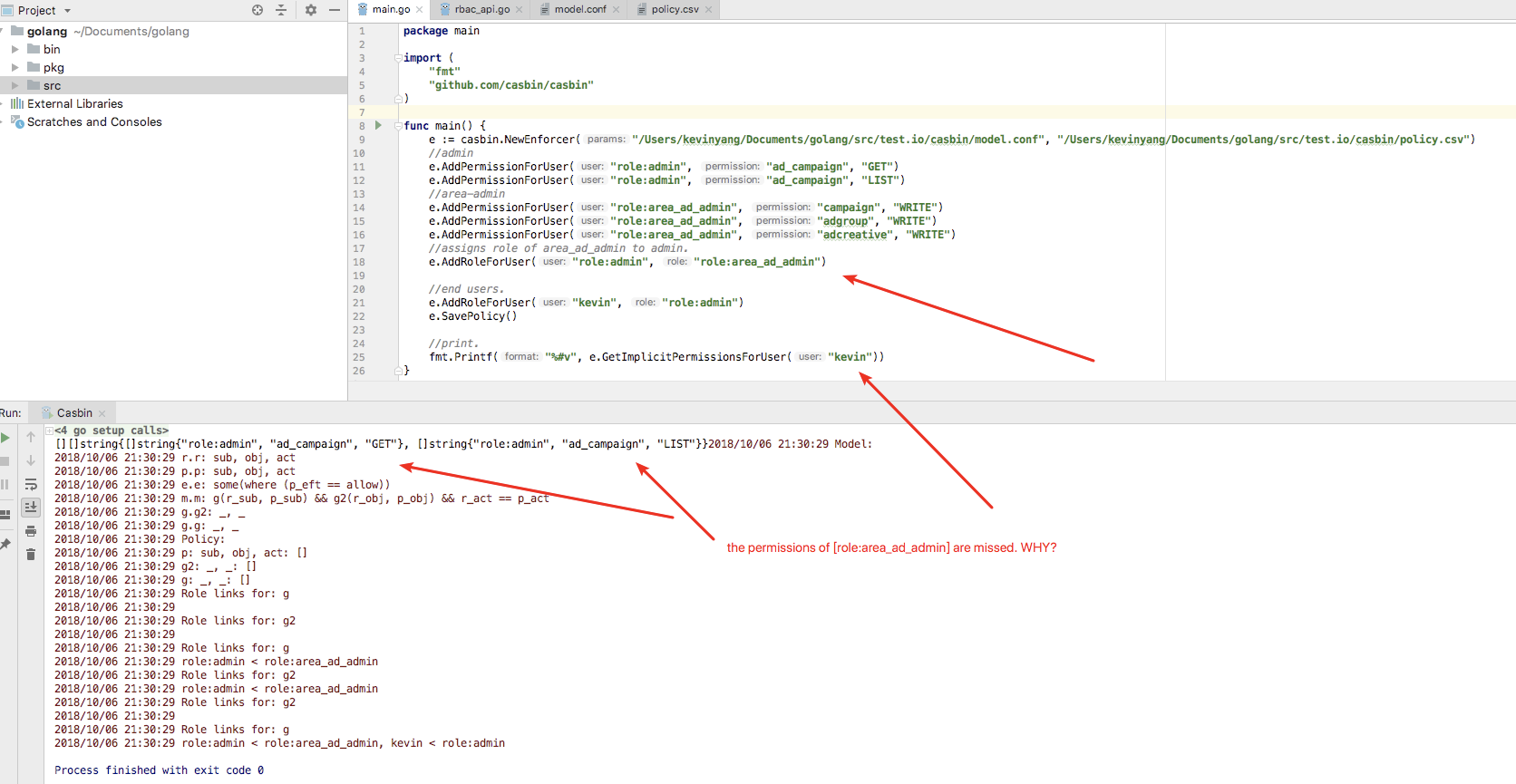
g0194776 commentedon Oct 6, 2018
@hsluoyz
It isn't my expected result. WHY?
hsluoyz commentedon Oct 6, 2018
Can you post your
main()body here? So I can copy and test it.g0194776 commentedon Oct 6, 2018
@hsluoyz OK.
code
model.conf
Add GetImplicitRolesForUser() to get implicit roles, fix: #137
hsluoyz commentedon Oct 6, 2018
It has been fixed, see: 3e0da64
g0194776 commentedon Oct 6, 2018
@hsluoyz
The bug fix code has been tested successfully. Thanks a lot.
Add GetImplicitPermissionsForUser() to get implicit permissions, fix: c…